Identify Confidentiality
Objective is to provide privacy to the subscriber. So that it will not be easy to identify the person from their signal over the radio and connections. In other words, it is the protection of data from disclosure to unauthorized third parties
Authentication
Provides assurance that a party in data communication is who or what they claim to be
Authorization
It is a security service which helps to ensure that a party may only perform the actions that they’re allowed to perform.
Availability
Means data services are always usable by the appropriate parties in the intended manner
GPRS threats
Overbilling attacks
Such attack is being started by a mobile station that consists of malware and it hijacks an IP address of another mobile station and invokes a download from a malicious server on the internet. After the download starts, the malicious mobile station exits the session. The mobile station that is being under attack, will receive the download traffic, and gets charged for traffic that wasn't used. The same malicious party can also execute this attack for sending of broadcasts of unsolicited data towards subscriber’s cell phones. The outcome is the same, the subscriber will be paying data usage that they did not solicited and might not have needed or wanted. Such attacks are not limited to the Gp interface.
GPRS Solutions
Overbilling attack prevention- Enables the GTP firewall to notify the Gi firewall of an attack. The firewall is then able to terminate the “hanging” sessions or tunnels, thus cutting off the unwanted traffic. This helps to prevent the GPRS subscriber from exceeding the limit.
Reference
http://www.brookson.com/gsm/gprs.pdf
Reference
http://www.brookson.com/gsm/gprs.pdf
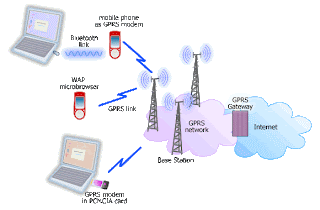
It could be better if you could put point form for the security features the layout will look more pleasant. The picture for the GPRS seem a bit off topic as it shows the architecture of the network rather than any security threats, as for the security features it is briefly explain so more explanation will make the blog information better and adding in more pictures and/or video will help with the explanation such as overbilling attacks, unilateral authentication as it is a bit dry and breaking it into smaller paragraph will make it much easier to read, and the type of font used is not consistent.
ReplyDeleteHi Kelly, the post is understandable and easy to read. Though inconsistent line spacing and font, it is easy to read and understand with the clear labelling of the sub topics. The sentences are short and are ideal for a post. It appeals to the readers as the sentences are short and not lengthy. Elaboration can be further explained for the security features. There is good explanation for the threats and solutions. An introduction on GPRS can be added to explain he diagram shown above or a brief explanation of what it is and what it is used for and some of the user who uses GPRS.
ReplyDelete