X.500 Directory service is a standard way to develop an electronic directory of people in an organization making it possible for it to be part of a global directory available to anyone in the world with internet access. The main idea is for it to be able to look up people in a user friendly way by either name, department or organization.
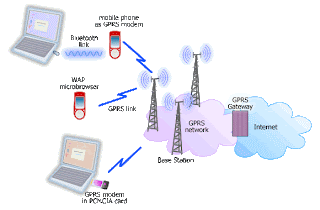
Information in an X.500 directory may be distributed or replicated among different directory servers. In Fig 1.1 is a sample of X.500 infrastructure. In the diagram, a directory server is called a Directory Server Agent(DSA) and the client which is accessing an X.500 directory is called a Directory User Agent (DUA). Also, a client may be a LightWeight Directory Access Protocol (LDAP) client.
Fig 1.1
Security Features of X.500
X.500 offers different level of authentication in order to handle different security requirements. The X.500 protocol uses X.509 Public Key Infrastructure for authentication.
1) It treats every computer and user as an object. It has a server, backup and a system admin. The database schema for each of them should be consistent. If there is a need to modify any of the schema to accommodate one of the data from one company that is not present, it won’t be able to do so.
2) It standardize the storage of files regarding user attributes and permissions.
3) They center on the individuals that wish to access to it rather than on a static list such as passwords.
Strong authentication
Establishes trust between X.500 directory components, authorize identity of directory users for access control and protects against denial of service attacks.
Reference